Hello folks!
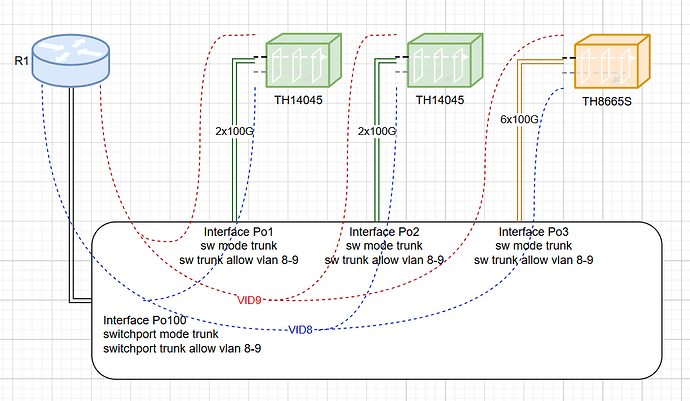
I have CGNv4 with a bunch of TH14045 in production with very simple topology “on the stick”, one LACP 2x100G, 2 vlans on all units (one for NAT in, one for NAT out). It’s serving traffic without any issue, no loopdetect in logs. Recently I got a pair of a new shiny TH8665S and tried to add it to the scheme.
Everything seems to work, but I got a spam for possible loop at TH8665S:
Aug 28 2025 17:19:52 Warning [ACOS]: - PU1 - Potential loop detected on Port 1 VLAN 9 Src MAC 001f.a0xx.x949 Dst MAC ffff.ffff.ffff
Aug 28 2025 17:19:38 Warning [ACOS]: - PU1 - Potential loop detected on Port 1 VLAN 8 Src MAC 001f.a0xx.x94a Dst MAC ffff.ffff.ffff
Aug 28 2025 17:17:12 Warning [ACOS]: - PU1 - Potential loop detected on Port 1 VLAN 9 Src MAC 001f.a0xx.x949 Dst MAC ffff.ffff.ffff
Aug 28 2025 17:16:58 Warning [ACOS]: - PU1 - Potential loop detected on Port 1 VLAN 8 Src MAC 001f.a0xx.x94a Dst MAC ffff.ffff.ffff
It keeps spamming even if I disable ethernet 1. Even if there is only one 100G port left in the LACP.
The configuration is very simple:
shared partition
vlan 8
tagged trunk 1
router-interface ve 8
vlan 9
tagged trunk 1
router-interface ve 9
interface ethernet 1
trunk-group 1 lacp
interface ethernet 3
enable
trunk-group 1 lacp
interface ethernet 5
enable
trunk-group 1 lacp
interface ethernet 7
enable
trunk-group 1 lacp
interface ethernet 9
enable
trunk-group 1 lacp
interface ethernet 11
enable
trunk-group 1 lacp
interface trunk 1
interface ve 8
ip address 10.yy.yy.yy 255.255.255.240
ip nat inside
interface ve 9
ip address 10.zz.zz.zz 255.255.255.240
ip nat outside
Mac learning works as expected:
A10-8665-1.CV19#sh switch mac-table
Mac Tables:
L2 Cache Table:
L2: ERROR: Feature unavailableL2 User Table:
mac=18:ef:63:xx:xa:75 vlan=8 GPORT=0x0 Trunk=1 Hit
mac=00:1f:a0:xx:x3:68 vlan=8 GPORT=0x0 Trunk=1 Hit
mac=18:ef:63:xx:xa:75 vlan=9 GPORT=0x0 Trunk=1 Hit
mac=00:1f:a0:xx:x3:69 vlan=9 GPORT=0x0 Trunk=1 Hit
mac=00:1f:a0:xx:x7:99 vlan=9 GPORT=0x0 Trunk=1 Hit
mac=00:1f:a0:xx:x2:49 vlan=9 GPORT=0x0 Trunk=1 Hit
mac=00:1f:a0:xx:x2:48 vlan=8 GPORT=0x0 Trunk=1 Hit
The upper switch doesn’t detect any mac-flapping. I even tried to tcpdump the port-channel to the 8665, and found nothing suspicious. Strange thing is that it’s always detected from PU1 and never from PU2. Software version 6.0.6-SP1, build 1 (Feb-03-2025,17:18)
I tried 2 different sites, and 2 different units, the behavior is almost the same. Somehow I managed to get rid of it by deleting/recreating LACP while randomly shutting/unshutting ethernet interfaces on the first site. But I can’t do the trick with the new one. Any ideas?