Hi,
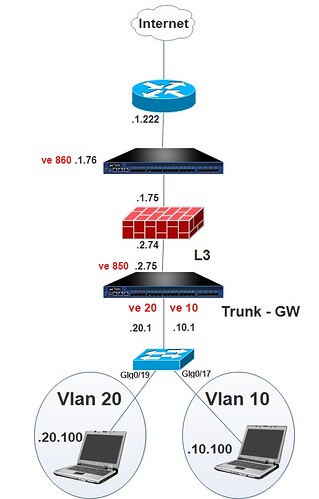
Before A10 Deployment, our Core firewall was doing the InterVlan Routing.
At the moment A10 does the InterVlan Routing. While we require the Core Firewall to do that, we do have 10s of restriction policies.
I have simulated this in a testing environment and appreciate your help.
Here is my full configuration,
system ve-mac-scheme system-mac ! terminal idle-timeout 0 ! partition ssli_innn id 1 ! partition ssli_iouttt id 2 ! web-service axapi-timeout-policy idle 0 ! interface management ip address 192.168.1.73 255.255.255.0 enable lldp enable rx tx ! interface ethernet 1 enable ! interface ethernet 2 enable ! interface ethernet 3 ! interface ethernet 4 ! interface ethernet 5 ! interface ethernet 6 ! interface ethernet 7 ! interface ethernet 8 ! interface ethernet 9 ! interface ethernet 10 ! interface ethernet 11 ! interface ethernet 12 ! ! end ! active-partition ssli_innn ! ! access-list 190 remark ssli_innn ! access-list 190 deny ip 192.168.0.0 0.0.255.255 192.168.0.0 0.0.255.255 ! access-list 190 permit ip any any ! access-list 191 remark block_quic ! access-list 191 deny udp any any eq 80 ! access-list 191 deny udp any any eq 443 ! access-list 191 permit ip any any ! vlan 10 tagged ethernet 1 router-interface ve 10 ! vlan 20 tagged ethernet 1 router-interface ve 20 ! vlan 850 untagged ethernet 2 router-interface ve 850 ! interface ethernet 1 enable ! interface ethernet 2 enable ! interface ve 10 access-list 191 in ip address 192.168.10.1 255.255.255.0 ip allow-promiscuous-vip ! interface ve 20 access-list 191 in ip address 192.168.20.1 255.255.255.0 ip allow-promiscuous-vip ! interface ve 850 ip address 192.168.2.75 255.255.255.0 ip allow-promiscuous-vip ! ! ip route 0.0.0.0 /0 192.168.2.74 ! slb template cipher cl_cipher_template TLS1_RSA_AES_128_SHA TLS1_RSA_AES_256_SHA TLS1_RSA_AES_128_GCM_SHA256 TLS1_RSA_AES_256_GCM_SHA384 TLS1_ECDHE_RSA_AES_128_SHA TLS1_ECDHE_RSA_AES_256_SHA TLS1_ECDHE_RSA_AES_128_SHA256 TLS1_ECDHE_RSA_AES_128_GCM_SHA256 ! slb server fw1 192.168.1.76 port 0 tcp health-check-disable port 0 udp health-check-disable port 8080 tcp health-check-disable ! slb service-group SG_SSLi_TCP tcp member fw1 0 ! slb service-group SG_SSLi_UDP udp member fw1 0 ! slb service-group SG_SSLi_Xlated tcp member fw1 8080 ! slb template client-ssl cl_ssl template cipher cl_cipher_template forward-proxy-ca-cert InsightA10SSLi forward-proxy-ca-key InsightA10SSLi forward-proxy-ocsp-disable forward-proxy-crl-disable forward-proxy-cert-expiry hours 168 forward-proxy-enable forward-proxy-failsafe-disable disable-sslv3 ! slb template http insertHeaders non-http-bypass service-group SG_SSLi_Xlated ! slb virtual-server SSLi_in_ingress 0.0.0.0 acl 190 port 0 tcp service-group SG_SSLi_TCP no-dest-nat port 0 udp service-group SG_SSLi_UDP no-dest-nat port 0 others service-group SG_SSLi_UDP no-dest-nat port 443 https service-group SG_SSLi_Xlated template http insertHeaders template client-ssl cl_ssl no-dest-nat port-translation ! end !!! !!! !!! ! active-partition ssli_iouttt ! ! access-list 191 remark ssli_iouttt ! access-list 191 permit ip any any ! vlan 860 untagged ethernet 5 to 6 router-interface ve 860 ! interface ethernet 5 enable ! interface ethernet 6 enable ! interface ve 860 ip address 192.168.1.76 255.255.255.0 ip allow-promiscuous-vip ! ! ip route 0.0.0.0 /0 192.168.1.222 ! ip route 192.168.10.0 /24 192.168.1.74 ! ip route 192.168.20.0 /24 192.168.1.74 ! slb template cipher sr_cipher_template TLS1_RSA_AES_128_SHA TLS1_RSA_AES_256_SHA TLS1_RSA_AES_128_GCM_SHA256 TLS1_RSA_AES_256_GCM_SHA384 TLS1_ECDHE_RSA_AES_128_SHA TLS1_ECDHE_RSA_AES_256_SHA TLS1_ECDHE_RSA_AES_128_SHA256 TLS1_ECDHE_RSA_AES_128_GCM_SHA256 ! slb template server-ssl sr_ssl forward-proxy-enable template cipher sr_cipher_template ! slb server GW 192.168.1.222 port 0 tcp health-check-disable port 0 udp health-check-disable port 443 tcp health-check-disable ! slb service-group GW_SSL_443 tcp member GW 443 ! slb service-group GW_TCP_0 tcp member GW 0 ! slb service-group GW_UDP_0 udp member GW 0 ! slb template http removeHeaders non-http-bypass service-group GW_SSL_443 ! slb virtual-server SSLi_out_ingress 0.0.0.0 acl 191 port 0 tcp source-nat auto service-group GW_TCP_0 use-rcv-hop-for-resp no-dest-nat port 0 udp source-nat auto service-group GW_UDP_0 use-rcv-hop-for-resp no-dest-nat port 0 others source-nat auto service-group GW_UDP_0 use-rcv-hop-for-resp no-dest-nat port 443 tcp source-nat auto service-group GW_TCP_0 use-rcv-hop-for-resp no-dest-nat port 8080 http source-nat auto service-group GW_SSL_443 use-rcv-hop-for-resp template http removeHeaders template server-ssl sr_ssl no-dest-nat port-translation ! end !Current config commit point for partition 2 is 0 & config mode is classical-mode